Homework 01: Security Basics
This assignment is worth 125 points. It serves as a warm-up to introduce you to a number of ideas that will be explored in more detail during the course of the semester. Partial credit will be given for all questions — it is in your best interest to not leave any blank. Some of these questions may require you to conduct research beyond what we learned in class. You are free to leverage any public resources you'd like to complete this assignment, but make sure to cite your sources in your answers. Refer to this course's honor code policy for more information on what is appropriate reuse.
For this assignment, record your responses to the following activities in the
README.md file in the homework01 folder of your assignments GitLab
repository and push your work (including any code you developed) by 11:59 PM Tuesday, January 28.
Activity 0: Branching
As discussed in class, each homework assignment must be completed in its own git branch; this will allow you to separate the work of each assignment and for you to use the merge request workflow.
First, follow these instructions to setup your git environment.
To create a homework01 branch in your local repository, follow the
instructions below:
$ cd path/to/cse-40567-sp20-assignments # Go to assignments repository $ git checkout master # Make sure we are in master branch $ git pull --rebase # Make sure we are up-to-date with GitLab $ git checkout -b homework01 # Create homework01 branch and check it out $ cd homework01 # Go into homework01 folder
Once these commands have been successfully performed, you are now ready to add, commit, and push any work required for this assignment.
Activity 1: Security Technology Assessment (10 Points)
Imagine that you work for a government services company that has put into place the following security mechanisms. To access sensitive government records, an employee needs to use a private network that is not directly connected to the Internet. Terminals connected to the private network are in a secure room that can only be entered after a legitimate user presents their biometric data (iris + fingerprint), which is matched at the door. Once inside, the user must login to the network via multi-factor authentication (password + one-time token). If authentication is successful, the government data, which is stored on an AES encrypted filesystem on a database server, becomes available to the employee. The connection between the employee's terminal and the database server is also encrypted via AES. An intrusion detection system monitors all authentication points and the private network. This setup is an example of what security strategy we've talked about in class? Explain the reasoning behind your answer.
Activity 2: Designing a Social Engineering Attack (10 Points)
After repeated security breaches, a major credit rating agency within the United States has locked down its network by patching security holes, removing unnecessary services, deploying strong encryption, and monitoring for attacks via an intrusion detection system. In the interest of further improving the security, you have been hired by the agency to perform a penetration test of this network. A thorough audit of the network reveals that the software defenses are indeed strong. However, as a student in Notre Dame's computer security class, you learned that social engineering is a highly effective attack even in circumstances where technical barriers prevent software-based remote compromise. Design a social engineering attack against this target network. You know that the agency employs a large full-time office staff, and contracts out some of its work to various service providers around the country. Provide the "script" you intend to use against one or more of these targets, and identify the way in which you will deliver it.
Activity 3: Two-Factor Authentication (10 Points)
We learned in class that two-factor authentication is an effective counter-measure to social engineering attacks where the objective is to steal a legitimate user's password. Many web applications rely on two-factor authentication through a mobile application like Okta Verify, which Notre Dame uses. In the most common use case, a user will provide their username and password to a website, and if those credentials are valid, receive a prompt to signal the Okta app to generate a one-time token. The user must then check the Okta app on their second-factor device to release the site-specific one-time authentication token, which will be sent to the website to finish logging in. If the login session is successful, or if the one-time token's time window before use expires, then the token will no longer be valid for future use. The security of this scheme is derived from the user having a secret on a device they control (e.g., a phone or tablet), which cannot be obtained by a social engineering attack against a web application's administrators. Imagine you are attacking an account that is making use of Okta. How can you thwart the two-factor authentication scheme to steal the user's credentials without compromising the device Okta is installed on, or manipulating the user's authentication configurations?
Activity 4: Passwords (10 Points)
Using one of the password generation schemes we learned about in class, generate a new password. Explain the steps you used to arrive at the password.
Pro Tip: generate another password using the same scheme, and start using it as your own. (Of course, don't report what it is in the answer to this homework question!)
Activity 5: Virtual Private Networks (10 Points)
If you haven't done so already, install and configure the Notre Dame VPN software (https://vpnaccess.nd.edu/). Always use it whenever you are off campus and need to access university computing resources. What basic attack class that we have discussed does the VPN software protect against? What is the algorithm that the Cisco AnyConnect software is using to provide encryption in the Notre Dame configuration? Provide your responses to these last two questions as the answer here.
Activity 6: Hack the Black Box Binary (25 Points)
Download this ELF 64-bit statically linked Linux binary program (it should execute on most 64-bit Linux systems). The program can be invoked in the following manner:
./blackbox -u ‹username› -p ‹password›where ‹username› is a username string and ‹password› is a password string that you supply. If you provide a correct set of credentials, the program will print the message "Access granted." to the terminal. If you provide something other than a correct set of credentials, it will print "Access denied." Your task is to find a valid set of credentials for this binary. (Hint: there are at least two ways you can hack it). Describe the method you used, and provide any code you developed to assist your analysis (pick your favorite language if you go this route).
Activity 7: Port Surfing (25 Points)
Behind each Internet service is a port, which is an interface between the network and a piece of software running on the server providing that service. In the network security portion of this class, we will learn quite a bit about ports, including how to scan for them and exploit the services they expose. But for now, let's get our feet wet with a small exercise that reveals some of what goes on behind the scenes of web browsing.
The netcat tool is a standard Unix network utility that is useful for many tasks, including opening raw connections to arbitrary ports. It is available on most Linux servers and can be installed on a Linux virtual machine running on your own computer. To connect to a remote port, the following syntax can be used from the command line:
$ nc ‹host› ‹port›where ‹host› is the IP address or hostname of the remote host and ‹port› is the numeric target port in the range 0-65535. Using this program instead of a proper client to probe ports can be awkward at first. But doing so is often rewarding from a penetration testing standpoint — information that client software does not show the user may be revealed. In some instances, like the following case of a connection to an ftp server, the service running on the port will immediately provide human-readable output:
$ nc speedtest.tele2.net 21
220 (vsFTPd 3.0.3)
quit
221 Goodbye.
Here the server helpfully identified itself as vsFTPd version 3.0.3, without us prompting it. We then typed the command 'quit' to terminate the connection. Note that not all servers will be this helpful right off the bat. For instance, when connecting to the web server for the University of Southern California, the server will wait patiently for input before sending anything:
$ nc www.usc.edu 80Your task in this question is to probe USC's webserver using raw HTTP protocol commands, after connecting via netcat, to identify the type of the web server software. Report this information, along with the input syntax you used to interface with the web server, as your answer to this question.
Activity 8: Hack a Black Box Web Authentication System (25 Points)
Consider the web application available via this link. The login interface is quite simple: a user must enter a valid password in the box to authenticate to the app:
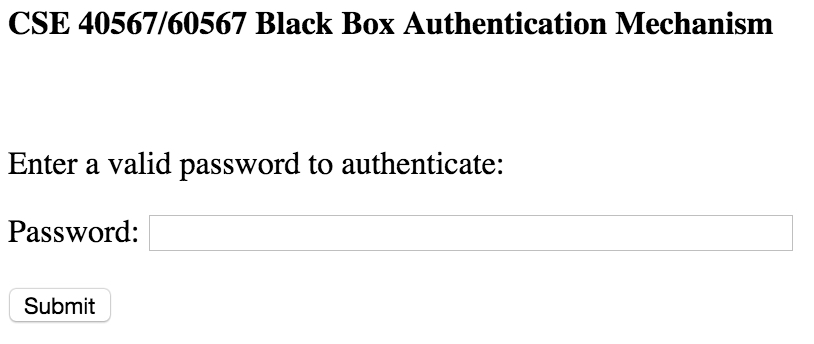
If you provide the correct password, the app will return the message "Authentication successful!". If you provide something other than the expected password, it will return the message "Incorrect password." Your task is to find out what this program's password is. (Hint: there are two ways you can hack it). Describe the method you used, and provide any code you developed to assist your analysis (pick your favorite language if you go this route).
Feedback
If you have any questions, comments, or concerns regarding the course, please
provide your feedback at the end of your README.md.
Submission
Remember to put your name in the README.md file. To submit your assignment, please commit your work to the homework01 folder
of your homework01 branch in your assignment's GitLab repository:
$ cd path/to/cse-40567-sp20-assignments # Go to assignments repository $ git checkout master # Make sure we are in master branch $ git pull --rebase # Make sure we are up-to-date with GitLab $ git checkout -b homework01 # Create homework01 branch and check it out $ cd homework01 # Go to homework01 directory ... $ $EDITOR README.md # Edit appropriate README.md $ git add README.md # Mark changes for commit $ git commit -m "homework01: complete" # Record changes ... $ git push -u origin homework01 # Push branch to GitLab
Procedure for submitting your work: create a merge request by the process that is described here, but make sure to change the target branch from wscheirer/cse-40567-sp20-assignments to your personal fork's master branch so that your code is not visible to other students. Additionally, assign this merge request to our TA (sabraha2) and add wscheirer as an approver (so all class staff can track your submission).